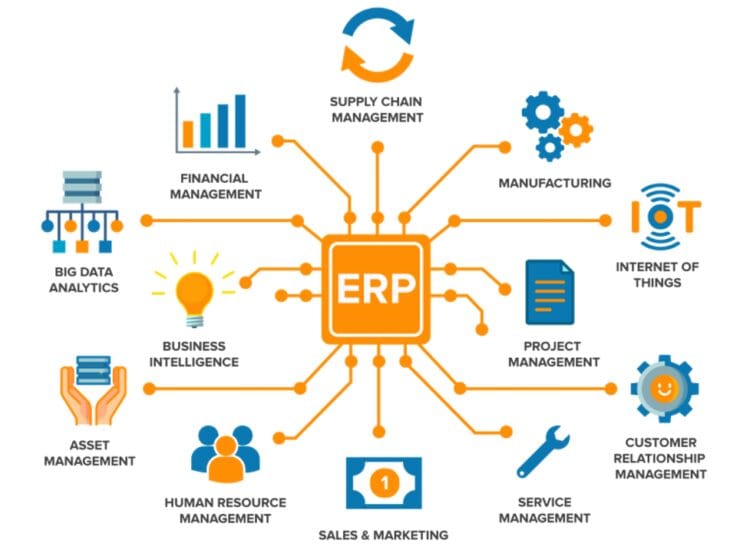
ERP system is an Industry term that denotes an Information technology solution use to integrate a broad set of activities and resources in an organization. An ERP system basically helps to shape and redefine businesses in the management of vital parts of its core business. The Structure and the information that is accrued from an ERP system facilitate optimal performance necessary for attaining organizational objectives. ERP is an acronym for Enterprise Resource Planning. The main feature of an ERP system is capacity to integrate businesses through application of modern technology and relevant business management practices. The integration of business processes with new information technology is critical towards success in the world of today. This integration has been transforming businesses to operate in modern information age. Necessarily to adapt to the new information age, organizations are forced to discard the traditional way of conducting business or managing organizational resources. Advancement of information technology Continue reading
Business Information Systems
What Is Business Intelligence (BI)? Architecture, Applications and Advantages
Business Intelligence is the process of discovering and analyzing data to make informed business decisions. The management in any business needs this aspect of management as part of the companies integral infrastructure in today’s world in order for the business to succeed. The data collected from many of the data collecting sources is used to determine trends, or measure, manage and improve on the performances of individuals, processes, teams and business units. The enterprise refers to any business organization that uses computers as an integral part of their business and relies on it for that businesses development. The History Of Business Intelligence In 1958, IBM researcher Hans Peter Luhn was the first one to use the term BI and he defined intelligence in his words: “the ability to apprehend the interrelationships of presented facts in such a way as to guide action towards a desired goal”. The business intelligence that Continue reading
Integration of Payroll System with HRIS
Computerization began in the human resource area via the payroll system. Payrolls are large masses of detailed information which need to be accurately and quickly updated. This is a fundamental accounting activity, so organizations had little hesitation in introducing such systems. Early systems were computer bureaus where data was processed outside the organization. Initially, it seemed that the promised benefits of computerization had finally arrived. The army of pay clerks was substantially reduced. However, new issues relating to input errors and processing delays soon arose. It is important for HR managers to understand this history because it explains why many early (and even some contemporary) HRIS have a bias towards payroll activities. Payroll processors first attempted to introduce Human Resource Information System (HRIS) in the mid-1970s when a major vendor offered a HR system with some additional fields of information that could be manipulated. Although a crude attempt Continue reading
Integration of Blockchain and Enterprise Resource Planning Systems
Blockchain Technology As a way to increase data security for transaction, a new system that allows these transactions to occur automatically more securely and without an intermediary has been conceived. Blockchain or (Distributed Ledger Technology) was developed in the aftermath of the 2008 recession to deliver transparency, security, and efficiency in managing transactions between multiple parties. This concept is now being implemented or considered in many business models worldwide. What really is Blockchain? In its simplest form, Blockchain can be described as a private, secure network that uses cryptography to keep exchanges secure, provides a decentralized database, or digital ledger, of transactions that everyone on the network can see. This network is essentially a chain of computers that must all approve an exchange before it can be verified and recorded. Following figure illustrates the Basic Blockchain Process. One of the benefits of this system is that once a record is Continue reading
Email Security Best Practices to Keep Your Business Safe
The most pervasive means of communication today for businesses and private citizens, Electronic mail or Email, was not designed with security in mind. Today, Email application is built into almost all smart devices from phones to computers to gaming and sensor devices. however, the Email message that this device send and receive is transmitted in plain text format in almost all cases. with ever-increasing cybercrime, sending plain text message that can potentially contain sensitive data is a risky undertaking. This weakness in security in Email systems, has made Email the primary attack vector for criminals. Cybercriminals use Email as simplest and cheapest method to ship their malicious payload to targets. The three core principles when it comes to information security, Confidentiality, Integrity and Availability (CIA) holds true in Email security as well. However, there is one other principle to consider in Email security, Non-repudiation meaning that the sender of the Continue reading
Case Study on Business Systems Planning And Implementation : McDonald’s Corporation
McDonald’s has worked hard to be more than a restaurant chain. It has become a marketing icon and is part of the routines of millions of people. Its success is so far reaching that it has developed its own culture and identity. It has become a symbol of the success and desirability of American popular culture. McDonald’s operates more than 24,000 restaurants in 114 countries. It has a 21 percent share of the very competitive US fast food industry. Overseas restaurants now account for half of the company’s profits. McDonald’s plans to open 10,000 new restaurants by the year 2005. It has been the forerunner in the recent industry trend of co-branding and satellite locations. What has set McDonald’s apart from the average hamburger restaurant is its ability to recognize customers’ needs and desires. It seems customers want fast, friendly service in a clean and orderly environment. McDonald’s Continue reading