Data Mining in the simplest terms, is a process of simplifying large data to generate valuable information or decluttering large amount of data to only extract useful information. Though the word “Data Mining” was not uttered until in 1980’s, when the term was trademarked by HNC to protect their product “DataBase Mining Workstation”, the concept of data mining was already established by Thomas Bayes in 1763. When Bayes published a theorem called Bayes theorem of looking at relationship between the current and prior probabilities. With the invention of computers, the theorem became a step stone to data mining as it allowed to understand reality based on the probabilities that are estimated. 1980’s was also the era which used algorithms to learn about relationships and what they mean by studying the data. Data Mining is a process that involves three elements, studying the relationship of the data, using machine to mimic Continue reading
Modern Information Systems
Case Study: IT Infrastructure Library (ITIL) Adoption by Disney
The Walt Disney Company is an internationally famous corporation that operates in the domains of media and entertainment. Having grown from a small cartoon studio, the company now operates in more than 40 countries around the world and includes such major departments as studios, parks, and experiences, and consumer products. The division of Theme Parks and Resorts is one of the busiest branches of the corporation, with 13 parks, over 40 resorts, and more than 118 million visitors each year. To succeed in such an environment, the Disney company adopted the best practices of IT service management as outlined in the Information Technology Infrastructure Library (ITIL). Informational Technology Infrastructure Library or ITIL is a group of practices designed to align IT services with the goals and vision of the business. It was originally developed in the 1980s and since then received regular revisions to suit the changes in technology and Continue reading
Decentralization in Cryptocurrencies
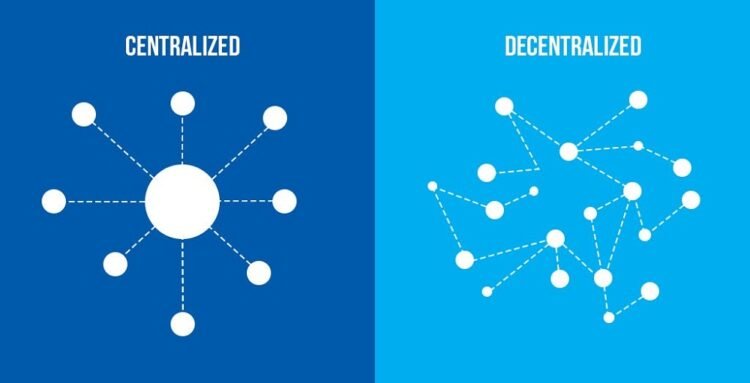
Decentralization is a defining characteristic of numerous cryptocurrencies and blockchain-based initiatives. By design, cryptocurrencies are decentralized and distributed, so there is no centralized authority or point of control. Decentralization in cryptocurrencies provides several benefits, including resistance to censorship and fraud, enhanced security, and better privacy. Decentralization carries several difficulties, particularly in terms of scalability and administration. Cryptocurrencies are a relatively young technology that is undergoing ongoing development. Therefore, there is no universal approach to Decentralization. Each project must carefully consider the involved trade-offs to develop a system that works. Adopting Decentralization in cryptocurrency makes firms more resilient and secure and gives users greater control over their finances. The policy enables investors to make independent decisions because the firm’s directives are not dependent on a specific authority. Consequently, this develops a system of trust, as the system must rely on its integrity to sustain the company’s longevity in the market. Decentralization Continue reading
Is Technology Hindering / Killing Creativity?
Recently, there have been numerous studies exploring the effects of technology on the youth population. Along with the significant growth in technology use, there are substantial gaps in knowledge about the rapid and sweeping changes it has on young people. Technology offers many benefits, including sustaining distance learning, improvements in communication, sustainable development, and transformation of goods and services. If it is universally accessible and used appropriately, technology can be a game-changer for the youth. It can significantly help address numerous problems regardless of a person’s disability, ethnicity, geographic isolation, or race. It can do so by providing youths with the knowledge and skills necessary to succeed in an increasingly digital world and connecting them to a world full of new opportunities. However, technology also has adverse effects on youth. Unarguably, technology is slowly reducing human’s imagination and creativity because people are highly dependent on the internet, are digitally distracted, Continue reading
Integration of Six Sigma into Enterprise Architecture (EA)
Today, more than ever before, enterprises are increasingly being faced with unparalleled competitive and regulatory demands, along with elevated levels of business uncertainty as they wade through the upsetting waters of contemporary global economy. On yet another front, the convergence of technology witnessed in the 21st century has made many enterprises increasingly concerned with how to productively transition to an enterprise exploiting information technology to its fullest strategic potential. In the light of these concerns, it is obvious that executives must embrace a paradigm shift from the traditional enterprise management approaches to more market-oriented approaches, which underlines the need to balance capabilities, manage risks, improve processes and systems, and engage in agile decision-making with a view to achieve the desired business end-states. As has been witnessed in the company, the organization’s Enterprise Architecture (EA) plays a critical role in this transition, particularly in integrating key processes and systems to enable Continue reading
Information Technology Infrastructure Library (ITIL) – An Overview
Information Technology Infrastructure Library (ITIL) is an approach to the information technology management service. It helps in practical understanding, identifying, and effective framework for planning and delivery supporting IT services in a given business. ITIL was formed in response to increasing dependence of businesses on information technology. ITIL was initially created under the backing of the UK government through CCTA department, which worked together with office of government commerce (OGC). The library is effective in defining structure of an organization through provision of skills of improving organizational information technology. It embraces standardized operational management practices and procedures, which help organizations operate IT infrastructure and achieve high quality service. The agency had set many recommendations to safeguard standard practices for both, government and private sectors in order to facilitate good IT management standards. The quantity of books increased from the initial publication in the year 1989 to about thirty volumes. More comprehensive books Continue reading