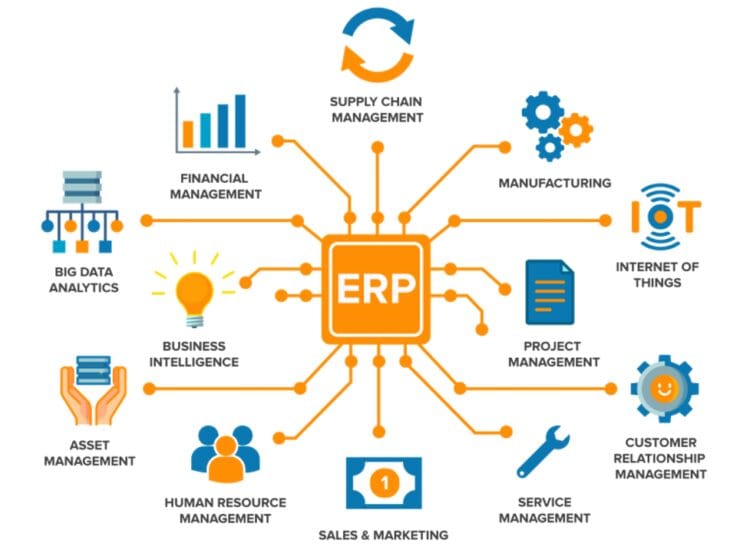
ERP system is an Industry term that denotes an Information technology solution use to integrate a broad set of activities and resources in an organization. An ERP system basically helps to shape and redefine businesses in the management of vital parts of its core business. The Structure and the information that is accrued from an ERP system facilitate optimal performance necessary for attaining organizational objectives. ERP is an acronym for Enterprise Resource Planning. The main feature of an ERP system is capacity to integrate businesses through application of modern technology and relevant business management practices. The integration of business processes with new information technology is critical towards success in the world of today. This integration has been transforming businesses to operate in modern information age. Necessarily to adapt to the new information age, organizations are forced to discard the traditional way of conducting business or managing organizational resources. Advancement of information technology Continue reading
Modern Information Systems
An Introduction to Computer Forensics
Forensic auditing deals with an extensive range of analytical work that is performed by expert accountants. This line of work typically involves an examination of the financial affairs of a company and is frequently connected with scrutinizing fraudulent activity. Forensic auditing consists of the entire investigation process, including having the investigator serve as an expert witness in a trial. Forensic accountants are even qualified to look into situations that are not fraud-related. These might include the settling of fiscal issues of a business or disputes between insurance claims. The forensic investigation encompasses the necessary steps taken to collect evidence in a suspected fraud case. The forensic audit is comparable to a financial audit, where a planning stage, an evidence gathering phase, a review procedure, and a client report, are implemented. The auditor uses a variety of audit techniques to recognize and assemble evidence. The auditor may want to find proof Continue reading
What Is Business Intelligence (BI)? Architecture, Applications and Advantages
Business Intelligence is the process of discovering and analyzing data to make informed business decisions. The management in any business needs this aspect of management as part of the companies integral infrastructure in today’s world in order for the business to succeed. The data collected from many of the data collecting sources is used to determine trends, or measure, manage and improve on the performances of individuals, processes, teams and business units. The enterprise refers to any business organization that uses computers as an integral part of their business and relies on it for that businesses development. The History Of Business Intelligence In 1958, IBM researcher Hans Peter Luhn was the first one to use the term BI and he defined intelligence in his words: “the ability to apprehend the interrelationships of presented facts in such a way as to guide action towards a desired goal”. The business intelligence that Continue reading
An Introduction to E-Services
E-services are important in B2C e-commerce for managing customer relations and enhancing sales. Rapidly advancement of technology such as wireless, broadband, smart cards, data warehousing, data mining and agent technologies, are contribute toward the effective accessibility and servicing of the correctly targeted customers for business while providing more choices, options and ultimately power to customers in their transactions with business. Further e-service provides a new business paradigm for the organizations operating in the electronic environment. There are three primary reasons for firms to develop e-services. Firstly, margin, consumer acquisition and service costs are generally much lower in an online medium versus that in an offline medium. Secondly, e-service inexpensively and effectively delivers high-quality, timely and in-depth product information desired by consumers. E-services also provide consumers with benefits such as better price quality comparisons and customized search processes based on criteria of importance. Finally, the use of e-services enables firms to Continue reading
Integration of Blockchain and Enterprise Resource Planning Systems
Blockchain Technology As a way to increase data security for transaction, a new system that allows these transactions to occur automatically more securely and without an intermediary has been conceived. Blockchain or (Distributed Ledger Technology) was developed in the aftermath of the 2008 recession to deliver transparency, security, and efficiency in managing transactions between multiple parties. This concept is now being implemented or considered in many business models worldwide. What really is Blockchain? In its simplest form, Blockchain can be described as a private, secure network that uses cryptography to keep exchanges secure, provides a decentralized database, or digital ledger, of transactions that everyone on the network can see. This network is essentially a chain of computers that must all approve an exchange before it can be verified and recorded. Following figure illustrates the Basic Blockchain Process. One of the benefits of this system is that once a record is Continue reading
Reasoning in Artificial Intelligence
The reasoning is deemed as the key logical element that provides the ability for human interaction in a given social environment. The key aspect associated with reasoning is the fact that the perception of a given individual is based on the reasons derived from the facts that relative to the environment as interpreted by the individual involved. This makes it clear that in a computational environment involving electronic devices or machines, the ability of the machine to deliver a given reason depends on the extent to which the social environment is quantified as logical conclusions with the help of a reason or combination of reasons. The major aspect associated with reasoning is that in the case of human reasoning the reasoning is accompanied by introspection which allows the individual to interpret the reason through self-observation and reporting of consciousness. This naturally provides the ability to develop resilience to exceptional situations Continue reading